Getting started on mitmproxy
mitmproxy is a free and open source interactive HTTPS proxy
The mitmproxy project's tools are a set of front-ends that expose common underlying functionality.
* mitmproxy is an interactive, SSL-capable intercepting proxy with a console interface.
* mitmdump is the command-line version of mitmproxy. Think tcpdump for HTTP.
* mitmweb is a web-based interface for mitmproxy.
* pathoc and pathod are perverse HTTP client and server applications designed to let you craft almost any conceivable HTTP request, including ones that creatively violate the standards.
Development setup
- Install python3
- (Windows) Start Windows PowerShell with the "Run as Administrator" option. Only members of the Administrators group on the computer can change the execution policy.
-
(Windows) Enable running unsigned scripts by entering:
set-executionpolicy remotesigned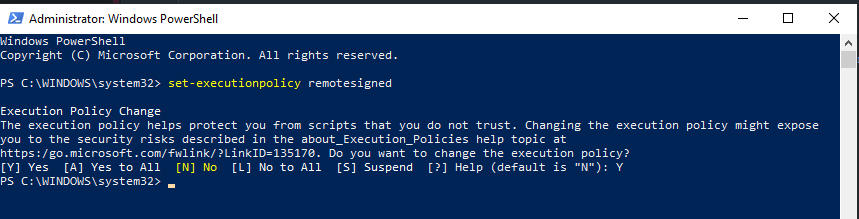
-
Install mitmproxy from source
(Windows)
powershell .\dev.ps1
./dev.sh
The dev script will create a virtualenv environment in a directory called "venv" and install all mandatory and optional dependencies into it. The primary mitmproxy components - mitmproxy and pathod - are installed as "editable", so any changes to the source in the repository will be reflected live in the virtualenv.
The main executables for the project - mitmdump, mitmproxy, mitmweb, pathod, and pathoc - are all created within the virtualenv. After activating the virtualenv, they will be on your $PATH, and you can run them like any other command:
(Windows)
venv\Scripts\activate
mitmdump --version
. venv/bin/activate
mitmdump --version
-
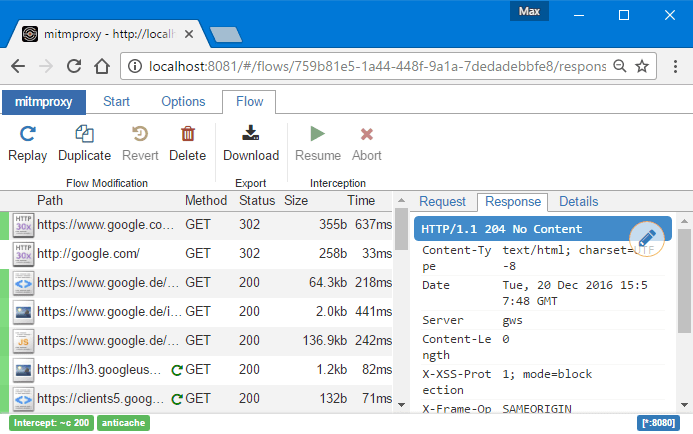
Running mitmweb
mitmweb --set block_global=false -
Set a lot of parameters if needed
mitmweb --set block_global=false --set ignore-hosts='^(?!example\.com)(?!mitmproxy\.org)' --set showhost=true --ssl-insecure -
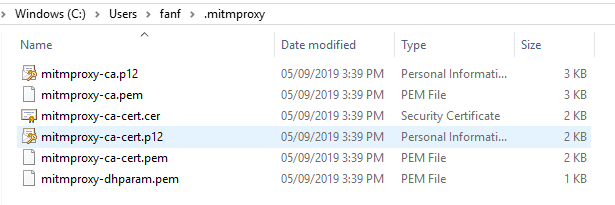
The certificate files locate at ~/.mitmproxy/. Apple/Android/Other could use .pem, Windows could use .p12
-
Set the proxy in WIFI configuration on the mobile with the IP of mitmproxy and port 8080